2 minutes
Major League Baseball Reflected XSS
Recently I have been looking for vulnerabilities such as XSS/CSRF within online applications and came across an XSS vulnerability within the Major League Basketball (MLB) website, which in question was vulnerable to reflected XSS. I did attempt responsible disclosure through Open Bug Bounty [3] and attempted contact via Twitter also, with no response returned and hence full disclosure.
In particular, the website was vulnerable within the “FORM_CODE” parameter with the payload of "--!><Svg/Onload=confirm(' OPENBUGBOUNTY')>" being used to exploit the reflected XSS vulnerability. (See below).
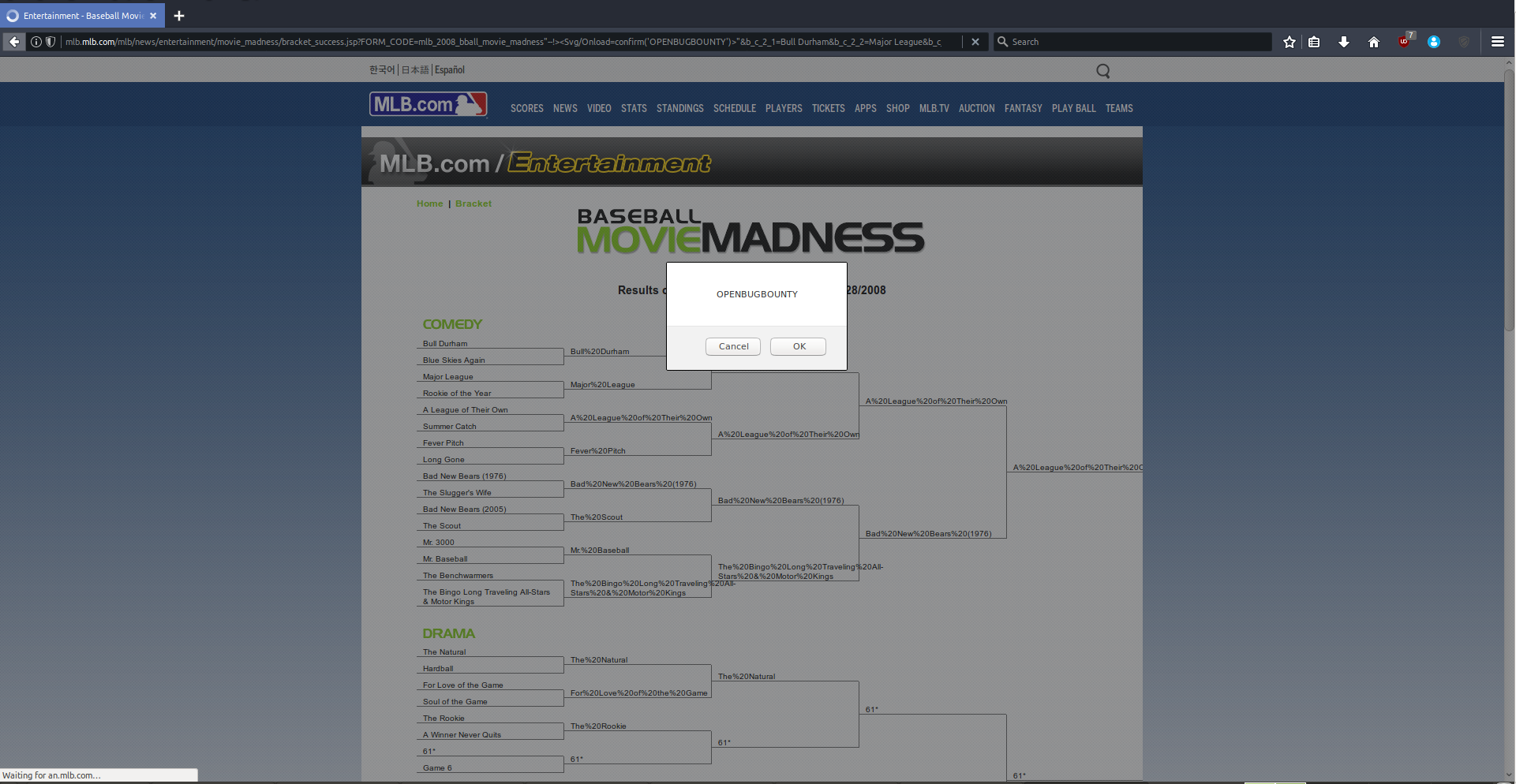
Vulnerability Information
The “FORM_CODE” parameter is vulnerable within the link rel and meta property tags, as shown below and within the above screenshots. (See https://pastebin.com/KztVKeFc for URL).
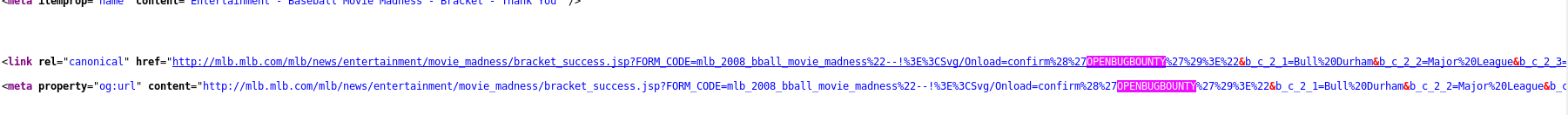
Feedback/Suggestions:
MLB should implement input filtering and encoding on all user supplied input to ensure raw XSS/HTML data is not executed within the user context [1][2].
Further Information:
[1] https://www.owasp.org/index.php/Cross-site_Scripting_(XSS) [2] https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet [3] https://www.openbugbounty.org/incidents/229173/
Disclosure Timeline:
29 April, 2017 at 12:22 GMT Vulnerability reported via Open Bug Bounty
1 May, 2017 at 06:31 GMT Vulnerability verified and confirmed
1 May, 2017 at 06:31 GMT Notification sent to generic security emails / Tweets sent to MLB.
1 May, 2017 at 06:31 GMT Notification sent to emails provided by researcher
1 May, 2017 at 10:17 GMT Notification sent to subscribers (without technical details)
29 May, 2017 at 07:15 GMT Vulnerability details publicly disclosed (Open Bug Bounty)
15 July, 2017 at 09:50 GMT Vulnerability details publicly disclosed (Blog)